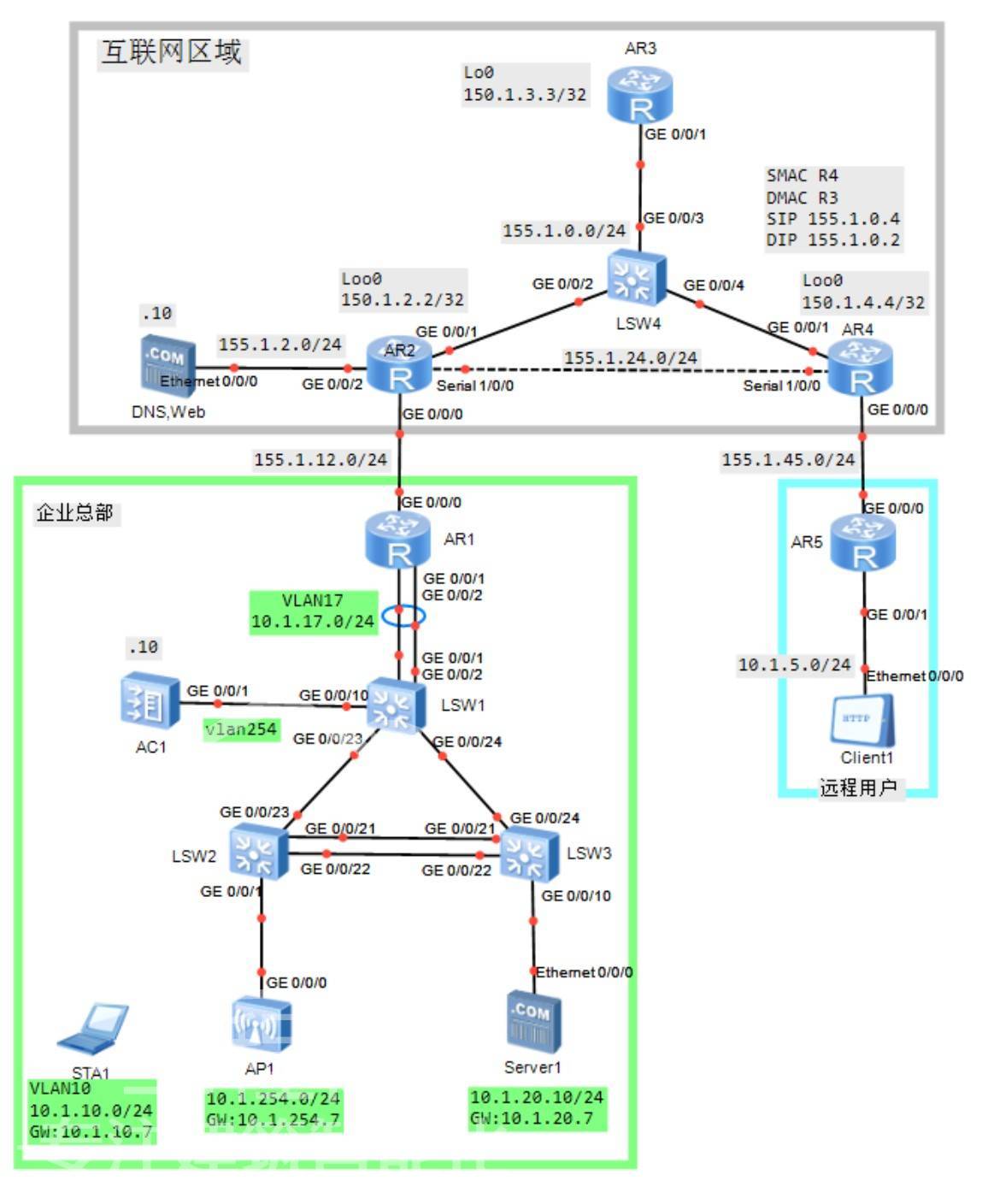
交换部分
1.S1,R1互联链路部置LACP链路聚合
2.S1, S2, S3互联部署Trunk,放行所有VLAN
S1,AC1互联仅放行必要VLAN
STP阻塞端口位置位于S3-G0/0/21,G0/0/22
3.S4部署Hybrid端口类型
实现R2,R4不能互通,但是能够与R3通信
4.设置VLAN10的网关位于S1 地址为10.1.10.7/24
VLAN20的网关位于S1 地址为10.1.20.7/24
路由部分
1.R1,S1互联部署0SPF区域0
2.R1上使用最少路由配置访问互联网
3.R2,R3,R4互联接口与Loopback0加入OSPF区域0,其他接口视情况加入
减少不必要的OSPF报文通告
*4.保障远程用户访问公网Web优先使用以太网链路
WAN部分
部署PPP
R2,R4互联部署PPP PAP认证,其中R4作为认证方,R2作为被认证方
账户密码:USER/HUAWEI
部署PPPoE
其中AR5作为PPPoE客户端,AR4作为PPPoE服务端
采用CHAP认证
拨号账户:USER/HUAWEI
避免数据分配,精确调整接口MTU
客户端根据拨号情况自动生成缺省路由
IP服务
3.S1对AP1与STA1分配地址
STA1通过S1获取地址(10.1.10.X/24,网关10.1.10.7)
AP地址总是自动获取为10.1.254.1/24,网关:10.1.254.7
STA1地址为10.1.10.10/24,
网关为10.1.10.7/24.
DNS为155.1.2.10
网络设备维护
1.配需R1仅接收STELNET网管
添加登录提示与登陆成功提示语
Stelnet登录闲置时间为15min
登录账户(USER/HUAWEI)
2.使用FTP备份配置到SERVER1
3.R1部署SNMPV3实现最高安全方式管理
用户名:USER用户组:USER_GROUP
密码:Huawei@123
对于接口UP/Down主动发送Trap信息
到主机10.1.20.10
V.WLAN部分
1.WLAN业务
管理VLAN:VLAN254
业务VLAN:VLAN10
转发模式:隧道模式
SSID:HUAWEI
安全策略:WPA2
密码:Huawei@123
加密算法:AES
2.WLAN组网方式
AP,AC位于相同子网
VI.ACL与NAT
1.R1禁止外网用户ping或tracert.
2.仅允许10.1.10.0/24的用户能够网管R1
3.R1获取公网地址155.1.12.11-155.1.12.20
部署NAPT实现10.1.10.0/24的任意用户可以访向公网
4.发布SERVER1的WEB服务到公网,
实现Client可以使用以下方式访问SERVER1
http://www.huawei.com:10080
(DNS已预配www.huawei.com对应155.1.12.10)
5.远程用户部署Easy-ip访问公网
通过访问公网Web服务器测试
解法:
交换部分
1.S1,R1互联链路部置LACP链路聚合
R1
interface Eth-Trunk1
undo portswitch #二层模式切换到三层模式
ip address 10.1.17.1 255.255.255.0
mode lacp-static #配置Eth-Trunk的工作模式,缺省情况下,Eth-Trunk的工作模式为手工负载分担模式。
trunkport GigabitEthernet 0/0/1 #增加成员接口
trunkport GigabitEthernet 0/0/2 #增加成员接口R1验证:
[r 1-Eth-Trunk1]display interface Eth-Trunk 1
Eth-Trunk1 current state : UP
Line protocol current state : UP
Last line protocol up time : 2024-03-24 09:57:11 UTC-08:00
Description:HUAWEI, AR Series, Eth-Trunk1 Interface
Route Port,Hash arithmetic : According to SIP-XOR-DIP,Maximal BW: 2G, Current BW
: 2G, The Maximum Transmit Unit is 1500
Internet Address is 10.1.17.1/24
IP Sending Frames' Format is PKTFMT_ETHNT_2, Hardware address is 00e0-fcdc-706b
Current system time: 2024-03-24 14:59:02-08:00
Input: 9871 packets, 1180744 bytes
Unicast: 0, Multicast: 9871
Broadcast: 0, Discard: 0
Total Error: 0
Output: 2669 packets, 330892 bytes
Unicast: 0, Multicast: 2668
Broadcast: 1, Discard: 0
Total Error: 0
Input bandwidth utilization : 0%
Output bandwidth utilization : 0%
-----------------------------------------------------
PortName Status Weight
-----------------------------------------------------
GigabitEthernet0/0/1 UP 1
GigabitEthernet0/0/2 UP 1
-----------------------------------------------------
The Number of Ports in Trunk : 2
The Number of UP Ports in Trunk : 2SW1
interface Eth-Trunk1
port link-type access
port default vlan 17
mode lacp-static
trunkport GigabitEthernet 0/0/1 #增加成员接口
trunkport GigabitEthernet 0/0/2 #增加成员接口 SW1验证:
[sw 1-Eth-Trunk1]display interface Eth 1
Eth-Trunk1 current state : UP
Line protocol current state : UP
Description:
Switch Port, PVID : 17, Hash arithmetic : According to SIP-XOR-DIP,Maximal BW:
2G, Current BW: 2G, The Maximum Frame Length is 9216
IP Sending Frames' Format is PKTFMT_ETHNT_2, Hardware address is 4c1f-cc60-2511
Current system time: 2024-03-24 15:01:58-08:00
Input bandwidth utilization : 0%
Output bandwidth utilization : 0%
-----------------------------------------------------
PortName Status Weight
-----------------------------------------------------
GigabitEthernet0/0/1 UP 1
GigabitEthernet0/0/2 UP 1
-----------------------------------------------------
The Number of Ports in Trunk : 2
The Number of UP Ports in Trunk : 22.S1, S2, S3互联部署Trunk,放行所有VLAN
SW1
vlan batch 17 254 10
interface GigabitEthernet0/0/10
port link-type trunk
port trunk pvid vlan 254
port trunk allow-pass vlan 254 10
interface GigabitEthernet0/0/23
port link-type trunk
port trunk allow-pass vlan 2 to 4094
interface GigabitEthernet0/0/24
port link-type trunk
port trunk allow-pass vlan 2 to 4094S1,AC1互联仅放行必要VLAN
AC1
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 17 254 SW1
interface GigabitEthernet0/0/10
port link-type trunk
port trunk pvid vlan 254
port trunk allow-pass vlan 254 10STP阻塞端口位置位于S3-G0/0/21,G0/0/22
SW1
stp mode rstp
stp instance 0 priority 0SW2
stp mode rstp
stp instance 0 priority 4096
interface Eth-Trunk2
port link-type trunk
port trunk allow-pass vlan 2 to 4094
mode lacp-static
trunkport GigabitEthernet 0/0/21
trunkport GigabitEthernet 0/0/22SW3
stp mode rstp
interface Eth-Trunk2
port link-type trunk
port trunk allow-pass vlan 2 to 4094
mode lacp-static
trunkport GigabitEthernet 0/0/21
trunkport GigabitEthernet 0/0/22 验证:
[SW3-Eth-Trunk2]display stp interface Eth-Trunk 2 brief
MSTID Port Role STP State Protection
0 Eth-Trunk2 ALTE DISCARDING NONE3.S4部署Hybrid端口类型 实现R2,R4不能互通,但是能够与R3通信
4.设置VLAN10的网关位于S1 地址为10.1.10.7/24 , VLAN20的网关位于S1 地址为10.1.20.7/24。
interface Vlanif10
ip address 10.1.10.7 255.255.255.0
dhcp select interface
#
interface Vlanif20
ip address 10.1.20.7 255.255.255.0
dhcp select interface路由部分
1.R1,S1互联部署0SPF区域0
R1
interface LoopBack0
ip address 10.10.10.2 255.255.255.255
#
ospf 1 router-id 10.10.10.2
area 0.0.0.0
network 10.1.17.1 0.0.0.0
network 10.10.10.2 0.0.0.0 SW1
interface LoopBack0
ip address 10.10.10.1 255.255.255.255
#
ospf 1 router-id 10.10.10.1
area 0.0.0.0
network 10.1.10.7 0.0.0.0
network 10.1.17.254 0.0.0.0
network 10.1.20.7 0.0.0.0
network 10.1.254.7 0.0.0.02.R1上使用最少路由配置访问互联网
R1
ip route-static 0.0.0.0 0.0.0.0 155.1.12.23.R2,R3,R4互联接口与Loopback0加入OSPF区域0,其他接口视情况加入, 减少不必要的OSPF报文通告。
R2
ospf 1 router-id 150.1.2.2
area 0.0.0.0
network 150.1.2.2 0.0.0.0
network 155.1.0.2 0.0.0.0
network 155.1.2.2 0.0.0.0
network 155.1.12.2 0.0.0.0 R3
ospf 1 router-id 150.1.3.3
area 0.0.0.0
network 150.1.3.3 0.0.0.0
network 155.1.0.3 0.0.0.0 R4
ospf 1 router-id 150.1.4.4
area 0.0.0.0
network 150.1.4.4 0.0.0.0
network 155.1.0.4 0.0.0.0
network 155.1.24.4 0.0.0.0
network 155.1.45.4 0.0.0.0 4.保障远程用户访问公网Web优先使用以太网链路
R4
interface Serial1/0/0
ospf cost 300WAN部分
部署PPP
R2,R4互联部署PPP PAP认证,其中R4作为认证方,R2作为被认证方 账户密码:USER/HUAWEI
R2
interface Serial1/0/0
link-protocol ppp
ppp timer negotiate 2
ppp pap local-user user password cipher huawei
ip address 155.1.24.2 255.255.255.0 R4
interface Serial1/0/0
link-protocol ppp
ppp authentication-mode pap
ppp timer negotiate 2
ip address 155.1.24.4 255.255.255.0
aaa
local-user user password cipher huawei
local-user user service-type ppp抓包验证:
Frame 13: 20 bytes on wire (160 bits), 20 bytes captured (160 bits) on interface 0
Point-to-Point Protocol
Address: 0xff
Control: 0x03
Protocol: Password Authentication Protocol (0xc023)
PPP Password Authentication Protocol
Code: Authenticate-Request (1)
Identifier: 1
Length: 16
Data
Peer-ID-Length: 4
Peer-ID: user
Password-Length: 6
Password: huawei
Frame 14: 52 bytes on wire (416 bits), 52 bytes captured (416 bits) on interface 0
Point-to-Point Protocol
Address: 0xff
Control: 0x03
Protocol: Password Authentication Protocol (0xc023)
PPP Password Authentication Protocol
Code: Authenticate-Ack (2)
Identifier: 1
Length: 48
Data
Message-Length: 43
Message: Welcome to use Quidway ROUTER, Huawei Tech. 部署PPPoE
其中AR5作为PPPoE客户端,AR4作为PPPoE服务端
采用CHAP认证
拨号账户:USER/HUAWEI
避免数据分配,精确调整接口MTU
客户端根据拨号情况自动生成缺省路由
R5
interface Dialer1
link-protocol ppp
ppp ipcp default-route #添加默认路由
ppp chap user user
ppp chap password cipher huawei
ppp ipcp dns admit-any #添加dns服务器地址
mtu 1492 #修改mtu
ip address ppp-negotiate #自动获得地址
dialer user user
dialer bundle 1
dialer timer idle 0
dialer-group 1
quit
interface GigabitEthernet0/0/0
pppoe-client dial-bundle-number 1 R4
ip pool 1
gateway-list 155.1.24.254
network 155.1.24.0 mask 255.255.255.0
#
interface Virtual-Template1
remote address pool 1
ip address 155.1.45.4 255.255.255.0
#
interface GigabitEthernet0/0/0
pppoe-server bind Virtual-Template 1IP服务
3.S1对AP1与STA1分配地址
STA1通过S1获取地址(10.1.10.X/24,网关10.1.10.7)
AP地址总是自动获取为10.1.254.1/24,网关:10.1.254.7
STA1地址为10.1.10.10/24,
网关为10.1.10.7/24.
DNS为155.1.2.10
SW1
interface Vlanif254
ip address 10.1.254.7 255.255.255.0
dhcp select interface
dhcp server dns-list 155.1.2.10网络设备维护
1.配需R1仅接收STELNET网管
添加登录提示与登陆成功提示语
Stelnet登录闲置时间为15min
登录账户(USER/HUAWEI)
2.使用FTP备份配置到SERVER1
R1
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
user privilege level 15
protocol inbound ssh
user-interface vty 16 20
[r 1]stelnet server enable
aaa
local-user user password cipher huawei
local-user user service-type sshSW1上检验
ssh client first-time enable
[sw 1]stelnet 10.1.17.1
Please input the username:user
Trying 10.1.17.1 ...
Press CTRL+K to abort
Connected to 10.1.17.1 ...
The server is not authenticated. Continue to access it? [Y/N] :y
Save the server's public key? [Y/N] :y
Error: Please choose 'YES' or 'NO' first before pressing 'Enter'. [Y/N]:y
Enter password:
<r 1>
<r 1>
<sw 1>ftp 10.1.20.10
Trying 10.1.20.10 ...
Press CTRL+K to abort
Connected to 10.1.20.10.
220 FtpServerTry FtpD for free
User(10.1.20.10:(none)):
331 Password required for .
Enter password:
230 User logged in , proceed
[ftp]
[ftp]put vrpcfg.zip
200 Port command okay.
150 Opening BINARY data connection for vrpcfg.zip
100%
226 Transfer finished successfully. Data connection closed.
FTP: 771 byte(s) sent in 0.170 second(s) 4.53Kbyte(s)/sec.
[ftp]dir
200 Port command okay.
150 Opening ASCII NO-PRINT mode data connection for ls -l.
drwxrwxrwx 1 nogroup 0 May 14 2023 CRT9.1
-rwxrwxrwx 1 nogroup 771 Mar 31 2024 vrpcfg.zip1.WLAN业务
管理VLAN:VLAN254
业务VLAN:VLAN10
转发模式:隧道模式
SSID:HUAWEI
安全策略:WPA2
密码:Huawei@123
加密算法:AES
SW1
interface GigabitEthernet0/0/10
port link-type trunk
port trunk pvid vlan 254
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 254AC
vlan batch 10 254
interface GigabitEthernet0/0/1
port link-type trunk
port trunk pvid vlan 254
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 17 254
[AC6605]capwap source interface Vlanif 254 #指定CAPWAP源接口
[AC6605]wlan
[AC6605-wlan-view]AP
[AC6605-wlan-view]ap auth-mode no-auth #选择AP上线认证模式
[AC6605-wlan-view]regulatory-domain-profile name cn #配置国家代码模板
[AC6605-wlan-regulate-domain-cn]country-code CN #p配置国家代码
[AC6605-wlan-view]ap-group name A #配置AP组名字为A
[AC6605-wlan-view]ap-id 0 #AP上线后 进入AP-id 配置名称及组
[AC6605-wlan-ap-0]ap-name a-1 #修改AP 名称
[AC6605-wlan-ap-0]ap-group a #将AP0加入A组
[AC6605-wlan-view]security-profile name hcia #配置安全模板
[AC6605-wlan-sec-prof-hcia]security wpa2 psk pass-phrase huawei@123 aes #配置加密算法和无线密码
[AC6605-wlan-view]ssid-profile name huawei #配置ssid模板
[AC6605-wlan-ssid-prof-IT]ssid huawei #配置ssid名称
[AC6605-wlan-view]vap-profile name A 配置Vap模板
[AC6605-wlan-vap-prof-a]service-vlan vlan-id 10 #配置业务通道
[AC6605-wlan-vap-prof-a]ssid-profile huawei #调用SSID 模板
[AC6605-wlan-vap-prof-a]security-profile hcia #调用安全模板
[AC6605-wlan-vap-prof-a]forward-mode direct-forward #定义为直接转发模式
#forward-mode tunnel #tunnel为隧道转发模式
[AC6605-wlan-view]ap-group name a #进入AP组
[AC6605-wlan-ap-group-a]vap-profile a wlan 1 radio all #AP组下调用VAP模板释放无线信号2.WLAN组网方式
AP,AC位于相同子网
VI.ACL与NAT
1.R1禁止外网用户ping或tracert.
1:配置ACL 3001筛选到公网IP地址的ICMP报文:
acl 3001
rule 5 deny icmp destination 155.1.12.1 0
2:配置流分类匹配ACL3001
traffic classifier test operator or
if-match acl 3001
3:配置流行为拒绝:
traffic behavior test
deny
4:配置流策略绑定流分类和流行为:
traffic policy test
classifier test behavior test
5:在公网接口应用流策略:
interface GigabitEthernet0/0/0
ip address 155.1.12.1 255.255.255.0
traffic-policy test inbound2.仅允许10.1.10.0/24的用户能够网管R1
acl number 2000
rule 5 permit source 10.1.10.0 0.0.0.255
rule 100 deny
user-interface con 0
authentication-mode AAA
user-interface vty 0 4
acl 2000 inbound #调用ACL
authentication-mode aaa
user privilege level 15
protocol inbound all
user-interface vty 16 20
quit
aaa
[r 1-aaa]local-user huawei password cipher huawei@123 privilege level 15
[r 1-aaa]local-user huawei service-type ssh telnet ftp web 3.R1获取公网地址155.1.12.11-155.1.12.20
部署NAPT实现10.1.10.0/24的任意用户可以访向公网
[r 1]nat address-group 1 155.1.12.11 155.1.12.20
interface GigabitEthernet0/0/0
ip address 155.1.12.1 255.255.255.0
[r 1-GigabitEthernet0/0/0]nat outbound 3000 address-group 14.发布SERVER1的WEB服务到公网,
实现Client可以使用以下方式访问SERVER1
http://www.huawei.com:10080
(DNS已预配www.huawei.com对应155.1.12.10)
5.远程用户部署Easy-ip访问公网
通过访问公网Web服务器测试
拓扑完成99%
附件列表